Nessus : A security vulnerability scanning tool
What Is The Nessus Professional System Requirement? | E ...
Nov 08, 2016 The Nessus vulnerability scanner products are annual subscription-based products sold through a sales partner or directly through the online Tenable Store. Nessus Cloud and Nessus Manager subscriptions are priced the same per number of hosts or agents; 128 hosts or agents costs $2,920, for example, while 256 hosts or agents costs $4,745. Nessus is the core of the Tenable network security product line, enabling organizations to address the ever-evolving challenge of understanding and mitigating their cybersecurity exposure. Download Nessus and Nessus Manager. Tenable GPG Key (Red Hat ES 6 / CentOS 6 / Oracle Linux 6 (including Unbreakable Enterprise Kernel) and newer, Fedora, Debian, Amazon Linux, Ubuntu). Description Nessus scanners will periodically go into an 'Initializing' state which occurs when the scanner is performing routine self-maintenance. Most notably (and the most time consuming) is re-indexing and building the plugin database. The 'Initializing' status is visible when attempting to navigate to the Nessus UI.
voted the #1 most useful security tool ! (www.insecure.org survey )
What is Nessus?
Nessus is a remote security scanning tool, which scans a computer and raises an alert if it discovers any vulnerabilities that malicious hackers could use to gain access to any computer you have connected to a network. It does this by running over 1200 checks on a given computer, testing to see if any of these attacks could be used to break into the computer or otherwise harm it.
Who would use a tool like this?
If you are an administrator in charge of any computer (or group of computers) connected to the internet, Nessus is a great tool help keep their domains free of the easy vulnerabilities that hackers and viruses commonly look to exploit.
What Nessus is NOT
Nessus is not a complete security solution, rather it is one small part of a good security strategy. Nessus does not actively prevent attacks, it is only a tool that checks your computers to find vulnerabilities that hackers COULD exploit. IT IS UP TO THE SYSTEM ADMINISTRATOR TO PATCH THESE VULNERABILITIES IN ORDER TO CREATE A SECURITY SOLUTION.
Why Nessus?
If you are familiar with other network vulnerability scanners, you might be wondering what advantages Nessus has over them. Key points include:
- Unlike other scanners, Nessus does not make assumptions about your server configuration (such as assuming that port 80 must be the only web server) that can cause other scanners to miss real vulnerabilities.
- Nessus is very extensible, providing a scripting language for you to write tests specific to your system once you become more familiar with the tool. Its also provides a plug-in interface, and many free plug-ins are available from theNessus plug-in site. These plugs are often specific to detecting a common virus or vulnerability.
- Up to date information about new vulnerabilities and attacks. The Nessus team updates the list of what vulnerabilities to check for on a daily basis in order to minimize the window between an exploit appearing in the wild, and you being able to detect it with Nessus.
- Open-source. Nessus is open source, meaning it costs nothing, and you are free to see and modify the source as you wish.
- Patching Assistance: When Nessus detects a vulnerability, it is also most often able to suggest the best way you can mitigate the vulnerability.
For other advantages/features of Nessus, see: http://www.nessus.org/features.html
How Nessus Works
To learn how Nessus and other port-scanning security tools work, it is necessary to understand different services (such as a web server, SMTP server, FTP server, etc) are accessed on a remote server. Most high-level network traffic, such as email, web pages, etc reach a server via a high-level protocol that is transmitted reliably by a TCP stream. To keep different streams from interfering with each other, a computer divides its physical connection to the network into thousands of logical paths, called ports. So if you want to talk to a web server on a given machine, you would connect to port #80 (the standard HTTP port), but if you wanted to connect to an SMTP server on that same machine you would instead connect to port #25.
Each computer has thousands of ports, all of which may or may not have services (ie: a server for a specific high-level protocol) listening on them. Nessus works by testing each port on a computer, determining what service it is running, and then testing this service to make sure there are no vulnerabilities in it that could be used by a hacker to carry out a malicious attack. Nessus is called a 'remote scanner' because it does not need to be installed on a computer for it to test that computer. Instead, you can install it on only one computer and test as many computers as you would like.
Installation:
Nessus comes in two parts, a server called nessusd and a client, which can by any of several options. The server is the part of Nessus that actually runs the tests, and the client is used to tell the server what tests to run on what computers.
The server exists only for Unix/Linux platforms, but there are clients available for Unix/Linux, Windows and Mac. Therefore, once the server is set up and running, an administrator can run regularly scheduled Nessus tests using a client written for almost any platform.
Go to www.nessus.org to download the most release release of Nessus. As of this date, the current release can be found athttp://www.nessus.org/nessus_2_0.html along with extremely simple installation instructions. This will install the Nessus server app and a client on the unix based machine (note: this includes Mac OS X and above with developer tools installed). After installing the server you will have to do a couple quick configuration options, such as adding a user, described here:http://www.nessus.org/demo/first.html.
To download and install a Windows client, look at: http://nessuswx.nessus.org/
Using Nessus (part 1): Running a Scan

To run a scan, you must have the Nessus server running on some machine, then start up a Nessus client. The client will look something like this:
The two most important tabs are 'Nessusd host', which allows you to enter in the IP address of the Nessus server you will connect to, as well as the username and password needed to connect to this server. The other critical tab is labeled 'Target Selection'. This is where you specify which host(s) you would like to scan. Each tab and field is covered in depth on this webpage :http://www.nessus.org/demo/second.html.
Once you are ready to scan, hit the 'Start the scan' button.
(note: for other clients, the exact behavior of the client my deviate from what is described here, but the overall concept is the same).
Using Nessus (part 2): Analyzing the Report
After a scan, Nessus clients typically offer to means to analyze the result. The client itself will often list each vulnerability found, gauging its level of severity and suggesting to the user how this problem could be fixed. An example screen is shown below:
Nessus clients are also able to generate more comprehensive and graphical reports in a variety of different formats. (see http://www.nessus.org/demo/third.html for examples) This can be very helpful if an administrator is scanning a large number of computers and would like to get an overall view of the state of the network.
More Information On Nessus:
The main Nessus website is www.nessus.org
Large quantities of Nessus documentation can be found at: http://www.nessus.org/documentation.html
Nessus's Freshmeat development page can be found at: http://www.freshmeat.net/projects/nessus/
This page was written by Dan Wendlandt for CS197.
Introduction
Nessus is one of the many vulnerability scanners used during vulnerability assessments and penetration testing engagements, including malicious attacks. This article will focus on this vulnerability scanner, discussing the fundamentals that one needs to have before getting started with the tool, the different scanning capabilities that it provides, what it takes to run the tool and how results appear once scans are complete.
Please note that this article does not in any way serve as a comprehensive guide to Nessus, but as an overview.
Nessus Products Brief
Nessus is sold by Tenable Security. The tool is free for non-enterprise use; however, for enterprise consumption, there are options that are priced differently. The following are the available options at your disposal:
- Tenable.io is a subscription-based service available here. It allows different teams to share scanners, schedules, scan policies and scan results. Tenable also contains what was previously known as Nessus Cloud, which used to be Tenable's Software-as-a-Service solution. Tenable.io also allows for the customization of workflows for effective vulnerability management.
- Nessus Agents provide a flexible way of scanning hosts within your environment without necessarily having to provide credentials to hosts. The agents enable scans to be carried out even when the hosts are offline. The application areas of these agents are wide. Consider environments that lack traditional malware protection, such as antivirus solutions — the overhead these agents exert within hosts is quite small. Here, agents take up minimal system resources within the hosts they are installed in, whilst still providing adequate malware protection.
- Nessus Professional is the most commonly-deployed vulnerability assessment solution across the industry. This solution helps you perform high-speed asset discovery, target profiling, configuration auditing, malware detection, sensitive data discovery and so much more. Nessus Professional runs on client devices such as laptops and can be effectively used by your security departments within your organization.
- Nessus Manager is used to provide the capabilities of the Nessus Professional solution along with numerous additional vulnerability management and collaboration features. However, Nessus Manager is no longer sold as of February 1st, 2018. This solution was used within organizations to collaborate and share information between different departments within the organization. It provided the ability to monitor company assets as well as devices in hard-to-reach environments.
These products discussed above offer multiple services that range from Web application scanning to mobile device scanning, cloud environment scanning, malware detection, control systems auditing (including SCADA and embedded devices) and configuration auditing and compliance checks.
Fundamentals of the Nessus Vulnerability Scanner
For us to appreciate the capabilities Nessus offers, we need to understand some fundamentals. We will first discuss the user interface and take a look at how to install Nessus on Linux and Windows Operating Systems.

What Is The Nessus Professional System Requirement? | E ...
Nov 08, 2016 The Nessus vulnerability scanner products are annual subscription-based products sold through a sales partner or directly through the online Tenable Store. Nessus Cloud and Nessus Manager subscriptions are priced the same per number of hosts or agents; 128 hosts or agents costs $2,920, for example, while 256 hosts or agents costs $4,745. Nessus is the core of the Tenable network security product line, enabling organizations to address the ever-evolving challenge of understanding and mitigating their cybersecurity exposure. Download Nessus and Nessus Manager. Tenable GPG Key (Red Hat ES 6 / CentOS 6 / Oracle Linux 6 (including Unbreakable Enterprise Kernel) and newer, Fedora, Debian, Amazon Linux, Ubuntu). Description Nessus scanners will periodically go into an 'Initializing' state which occurs when the scanner is performing routine self-maintenance. Most notably (and the most time consuming) is re-indexing and building the plugin database. The 'Initializing' status is visible when attempting to navigate to the Nessus UI.
voted the #1 most useful security tool ! (www.insecure.org survey )
What is Nessus?
Nessus is a remote security scanning tool, which scans a computer and raises an alert if it discovers any vulnerabilities that malicious hackers could use to gain access to any computer you have connected to a network. It does this by running over 1200 checks on a given computer, testing to see if any of these attacks could be used to break into the computer or otherwise harm it.
Who would use a tool like this?
If you are an administrator in charge of any computer (or group of computers) connected to the internet, Nessus is a great tool help keep their domains free of the easy vulnerabilities that hackers and viruses commonly look to exploit.
What Nessus is NOT
Nessus is not a complete security solution, rather it is one small part of a good security strategy. Nessus does not actively prevent attacks, it is only a tool that checks your computers to find vulnerabilities that hackers COULD exploit. IT IS UP TO THE SYSTEM ADMINISTRATOR TO PATCH THESE VULNERABILITIES IN ORDER TO CREATE A SECURITY SOLUTION.
Why Nessus?
If you are familiar with other network vulnerability scanners, you might be wondering what advantages Nessus has over them. Key points include:
- Unlike other scanners, Nessus does not make assumptions about your server configuration (such as assuming that port 80 must be the only web server) that can cause other scanners to miss real vulnerabilities.
- Nessus is very extensible, providing a scripting language for you to write tests specific to your system once you become more familiar with the tool. Its also provides a plug-in interface, and many free plug-ins are available from theNessus plug-in site. These plugs are often specific to detecting a common virus or vulnerability.
- Up to date information about new vulnerabilities and attacks. The Nessus team updates the list of what vulnerabilities to check for on a daily basis in order to minimize the window between an exploit appearing in the wild, and you being able to detect it with Nessus.
- Open-source. Nessus is open source, meaning it costs nothing, and you are free to see and modify the source as you wish.
- Patching Assistance: When Nessus detects a vulnerability, it is also most often able to suggest the best way you can mitigate the vulnerability.
For other advantages/features of Nessus, see: http://www.nessus.org/features.html
How Nessus Works
To learn how Nessus and other port-scanning security tools work, it is necessary to understand different services (such as a web server, SMTP server, FTP server, etc) are accessed on a remote server. Most high-level network traffic, such as email, web pages, etc reach a server via a high-level protocol that is transmitted reliably by a TCP stream. To keep different streams from interfering with each other, a computer divides its physical connection to the network into thousands of logical paths, called ports. So if you want to talk to a web server on a given machine, you would connect to port #80 (the standard HTTP port), but if you wanted to connect to an SMTP server on that same machine you would instead connect to port #25.
Each computer has thousands of ports, all of which may or may not have services (ie: a server for a specific high-level protocol) listening on them. Nessus works by testing each port on a computer, determining what service it is running, and then testing this service to make sure there are no vulnerabilities in it that could be used by a hacker to carry out a malicious attack. Nessus is called a 'remote scanner' because it does not need to be installed on a computer for it to test that computer. Instead, you can install it on only one computer and test as many computers as you would like.
Installation:
Nessus comes in two parts, a server called nessusd and a client, which can by any of several options. The server is the part of Nessus that actually runs the tests, and the client is used to tell the server what tests to run on what computers.
The server exists only for Unix/Linux platforms, but there are clients available for Unix/Linux, Windows and Mac. Therefore, once the server is set up and running, an administrator can run regularly scheduled Nessus tests using a client written for almost any platform.
Go to www.nessus.org to download the most release release of Nessus. As of this date, the current release can be found athttp://www.nessus.org/nessus_2_0.html along with extremely simple installation instructions. This will install the Nessus server app and a client on the unix based machine (note: this includes Mac OS X and above with developer tools installed). After installing the server you will have to do a couple quick configuration options, such as adding a user, described here:http://www.nessus.org/demo/first.html.
To download and install a Windows client, look at: http://nessuswx.nessus.org/
Using Nessus (part 1): Running a Scan
To run a scan, you must have the Nessus server running on some machine, then start up a Nessus client. The client will look something like this:
The two most important tabs are 'Nessusd host', which allows you to enter in the IP address of the Nessus server you will connect to, as well as the username and password needed to connect to this server. The other critical tab is labeled 'Target Selection'. This is where you specify which host(s) you would like to scan. Each tab and field is covered in depth on this webpage :http://www.nessus.org/demo/second.html.
Once you are ready to scan, hit the 'Start the scan' button.
(note: for other clients, the exact behavior of the client my deviate from what is described here, but the overall concept is the same).
Using Nessus (part 2): Analyzing the Report
After a scan, Nessus clients typically offer to means to analyze the result. The client itself will often list each vulnerability found, gauging its level of severity and suggesting to the user how this problem could be fixed. An example screen is shown below:
Nessus clients are also able to generate more comprehensive and graphical reports in a variety of different formats. (see http://www.nessus.org/demo/third.html for examples) This can be very helpful if an administrator is scanning a large number of computers and would like to get an overall view of the state of the network.
More Information On Nessus:
The main Nessus website is www.nessus.org
Large quantities of Nessus documentation can be found at: http://www.nessus.org/documentation.html
Nessus's Freshmeat development page can be found at: http://www.freshmeat.net/projects/nessus/
This page was written by Dan Wendlandt for CS197.
Introduction
Nessus is one of the many vulnerability scanners used during vulnerability assessments and penetration testing engagements, including malicious attacks. This article will focus on this vulnerability scanner, discussing the fundamentals that one needs to have before getting started with the tool, the different scanning capabilities that it provides, what it takes to run the tool and how results appear once scans are complete.
Please note that this article does not in any way serve as a comprehensive guide to Nessus, but as an overview.
Nessus Products Brief
Nessus is sold by Tenable Security. The tool is free for non-enterprise use; however, for enterprise consumption, there are options that are priced differently. The following are the available options at your disposal:
- Tenable.io is a subscription-based service available here. It allows different teams to share scanners, schedules, scan policies and scan results. Tenable also contains what was previously known as Nessus Cloud, which used to be Tenable's Software-as-a-Service solution. Tenable.io also allows for the customization of workflows for effective vulnerability management.
- Nessus Agents provide a flexible way of scanning hosts within your environment without necessarily having to provide credentials to hosts. The agents enable scans to be carried out even when the hosts are offline. The application areas of these agents are wide. Consider environments that lack traditional malware protection, such as antivirus solutions — the overhead these agents exert within hosts is quite small. Here, agents take up minimal system resources within the hosts they are installed in, whilst still providing adequate malware protection.
- Nessus Professional is the most commonly-deployed vulnerability assessment solution across the industry. This solution helps you perform high-speed asset discovery, target profiling, configuration auditing, malware detection, sensitive data discovery and so much more. Nessus Professional runs on client devices such as laptops and can be effectively used by your security departments within your organization.
- Nessus Manager is used to provide the capabilities of the Nessus Professional solution along with numerous additional vulnerability management and collaboration features. However, Nessus Manager is no longer sold as of February 1st, 2018. This solution was used within organizations to collaborate and share information between different departments within the organization. It provided the ability to monitor company assets as well as devices in hard-to-reach environments.
These products discussed above offer multiple services that range from Web application scanning to mobile device scanning, cloud environment scanning, malware detection, control systems auditing (including SCADA and embedded devices) and configuration auditing and compliance checks.
Fundamentals of the Nessus Vulnerability Scanner
For us to appreciate the capabilities Nessus offers, we need to understand some fundamentals. We will first discuss the user interface and take a look at how to install Nessus on Linux and Windows Operating Systems.
1. Installation on Linux
The downloadable installer can be found here for Linux-based systems. You need to make sure you know the distribution of Linux you are running in order to choose which installer to download. For instance, this article covers the Debian file system that Kali Linux is based on, so we will be downloading the *.deb installer file. We are also running a 64-bit version of Kali Linux; you'll need to find out the architecture you are running.
As of the writing of this article, the latest version of Nessus is 8.0.0.
Once the package file has been downloaded, you may install it from within the Linux terminal using the command below:
If you are using any other version of Linux, use the commands below:
For RedHat version 6:
For FreeBSD version 10:
After installation on your Linux system, be sure to start up the Nessus daemon as shown below:
For Red Hat, CentOS, Oracle Linux, Fedora, SUSE and FreeBSD, use the command below:
For Debian/Kali and Ubuntu, use the command below:
2. Installation on Windows
You can obtain the Windows installer here. Remember to download according to your architecture and operating system. Once downloaded, double-click on the installer and finish the installation by going through the wizard. You might be prompted to install WinPcap; if so, proceed with that installation as well.
Understanding the User Interface
After installation and during your first run, you will be required to activate your product based on the license type you intend to install. The exact steps for each of the products can be found here. After the license is activated, it is time to get down to running your Nessus scanner.
The Nessus user interface is primarily made up of two main pages: the scans page and the settings page. These pages allow you to manage scan configurations and set up the scanner according to how you would like it to perform within your system. You access these pages from the tab panel shown below.
As you can see, the user you created and any other notifications appear at the top right corner.
1. Scans Page
This page will allow you to create your new scans and manage them. You will also note that at the bottom left section of your screen, you have sections that allow you to configure policies that will apply to your scans, define plugin rules and monitor your scanners and agents as well. When you create a new scan or policy, a Scan Template or Policy Template appears.
2. Settings Page
Your settings page will contain configuration information, allowing you to define settings for your LDAP, Proxy and SMTP server for additional functionality and integration within your network.
At the bottom of your left screen you will also have access to your account, users and group settings.
Nessus Tenable Scanner Installer
Vulnerability Scanning With Nessus
Nessus performs its scans by utilizing plugins, which run against each host on the network in order to identify vulnerabilities. Plugins can be thought of as individual pieces of code that Nessus uses to conduct individual scan types on targets. Plugins are numerous and wide in their capabilities. For instance, a plugin could be launched and targeted at a host to:
- Identify which operating systems and services are running on which ports
- Identify which software components are vulnerable to attacks (FTP, SSH, SMB and more)
- Identify if compliance requirements are met on various hosts
The steps that are followed during scanning can be summarized in the image below:
When you launch a scan, Nessus goes through a series of steps.
Step 1: Nessus will retrieve the scan settings. The settings will define the ports to be scanned, the plugins to be enabled and policy preferences definitions.
Step 2: Nessus will then perform host discovery to determine the hosts that are up. The protocols used in host discovery will be ICMP, TCP, UDP and ARP. You can specify these per your desires.
Step 3: Nessus then performs a port scan of each host that is discovered to be up. You can also define which ports you will want scanned. Ports can be defined in ranges or individually, with valid ports ranging from 1 to 65535.
Step 4: Nessus will then perform service detection to determine the services that are running behind each port on each host discovered
Step 5: Nessus then performs operating system detection.
Step 6: Once all the steps are complete, Nessus runs each host against a database of known vulnerabilities in an attempt to discover which host contains which vulnerabilities.
The image below summarizes these steps:
Configuring a Nessus Scan
Nessus gives you the ability to configure your scan based on different scan and policy templates. The description of each scan template can be found here. These templates will determine the settings that will be found within the scan policy settings. The following are the general settings that can be accessed:
Tenable Introduces Agent-Based Scanning In Nessus Manager
Basic: With this setting, you can specify security-related and organizational aspects of the scan or policy. These aspects will include the name of the scan, the targets of the scan, whether or not it is scheduled and who has access to it. The sections available within the basic settings can be found here.
Discovery: This is where you would define the ports to be scanned and the methods to be used while conducting this discovery. There are some sections within this setting that you should take a look at. They can be found here.
Assessment: This setting allows you to determine the type of vulnerability scan to perform and how they are performed. Nessus will check susceptibility of Web applications to attacks and other systems to brute-force attacks as well. This setting has sections that allow you to customize general scans to Windows, SCADA, Web applications, and even brute-force checks.
Report: This setting will allow you to determine how scan reports are generated and the information that should be included within them.
Advanced: Here you will define scan efficiency and the operations that the scan should perform. You will also be able to enable scan debugging here. You can find more information on the sections contained in this setting here.
Launching a Nessus Scan
Tenable Nessus Scanner Default Login
To perform a vulnerability scan, you would need to navigate your browser to the link https://localhost:8834. See below:
Hit the 'New Scan' button above, then select the type of scan to perform from the numerous templates available.
The templates shown above will be limited within the free version of Nessus. Your license will determine the version of Nessus you use. These templates will be more in number and capability for the commercial version.
As can be seen above, you would then issue your targets. Nessus is capable of performing scans on multiple targets separated by commas or issued in CIDR format. Once done, you will be redirected to the screen below.
Click the 'play' icon to launch your configured scan. It is possible to have multiple configured scans, allowing you to perform multiple scans. In the screen above, we configured just one scan. Below, you can however see results from two hosts summarizing the severity and instances of issues discovered.
(This has been included to demonstrate how results from multiple hosts appear).
Tenable Nessus Scanners
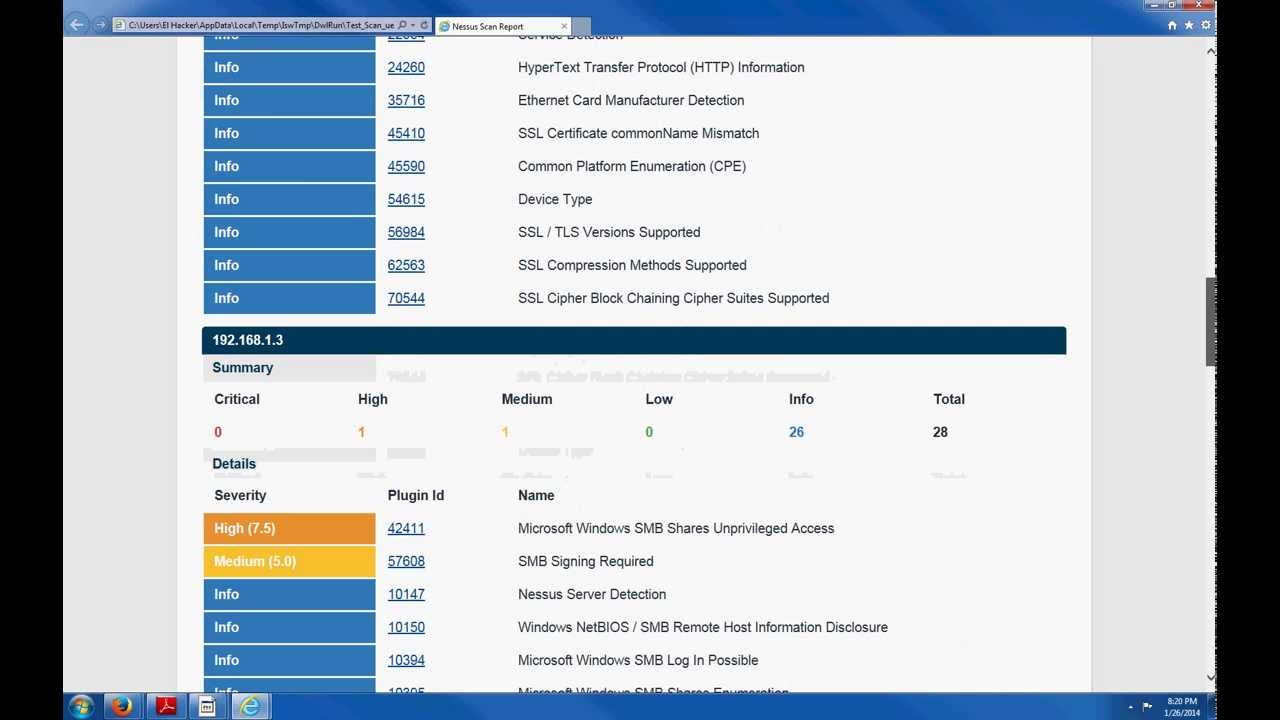
Nessus even allows you to drill down to specific hosts and vulnerabilities and get more information on how they were discovered, together with recommendations on how to patch identified risks. See below:
Conclusion
More Nessus Tenable Scanner Images
The Nessus Vulnerability Scanner is one of the most common vulnerability scanners in the cybersecurity industry today. The functionality that you get, especially with the commercial version, is total guarantee of value for your money. While it is also important to confirm your vulnerability hits by running other vulnerability scanners against your targets to eliminate the possibility of any false positives, Nessus's functions justify its popularity.
Sources
Tenable Nessus Vulnerability Scanner: Product Overview, TechTarget
Welcome to Nessus, Tenable
Tenable Nessus Scanner Connection Error
Scan Overview, Tenable
